Introduction to Microsoft Sentinel's User and Entity Behavior Analytics
IPs, Hosts, Users, oh my!
As SOC analysts work to defend their enterprises from a host of threats, one of the more difficult activities is understanding what is “normal.” Getting a sense of baseline activities across a variety of different business scenarios can be daunting, especially if your organization allows for a remote workforce and a variety of privileged functions across departments. What if Sentinel could help you with that by correlating logs and alerts from multiple data sources to establish a baseline on a per-entity basis?
What is Sentinel’s User and Entity Behavior Analytics
User and Entity Behavior Analytics (UEBA) allows Sentinel to collect logs and alerts from different data sources and build baseline profiles for entities within an organization. Entities can be IP addresses, host devices, users, and applications. Sentinel will analyze this data over time and leverage machine learning capabilities to identify anomalous activity. With all this data, Sentinel can help determine if an entity has been compromised and the blast radius of the compromise and its potential impact. This gives analysts easy prioritization when conducting an investigation or responding to an incident.
How does UEBA Work?
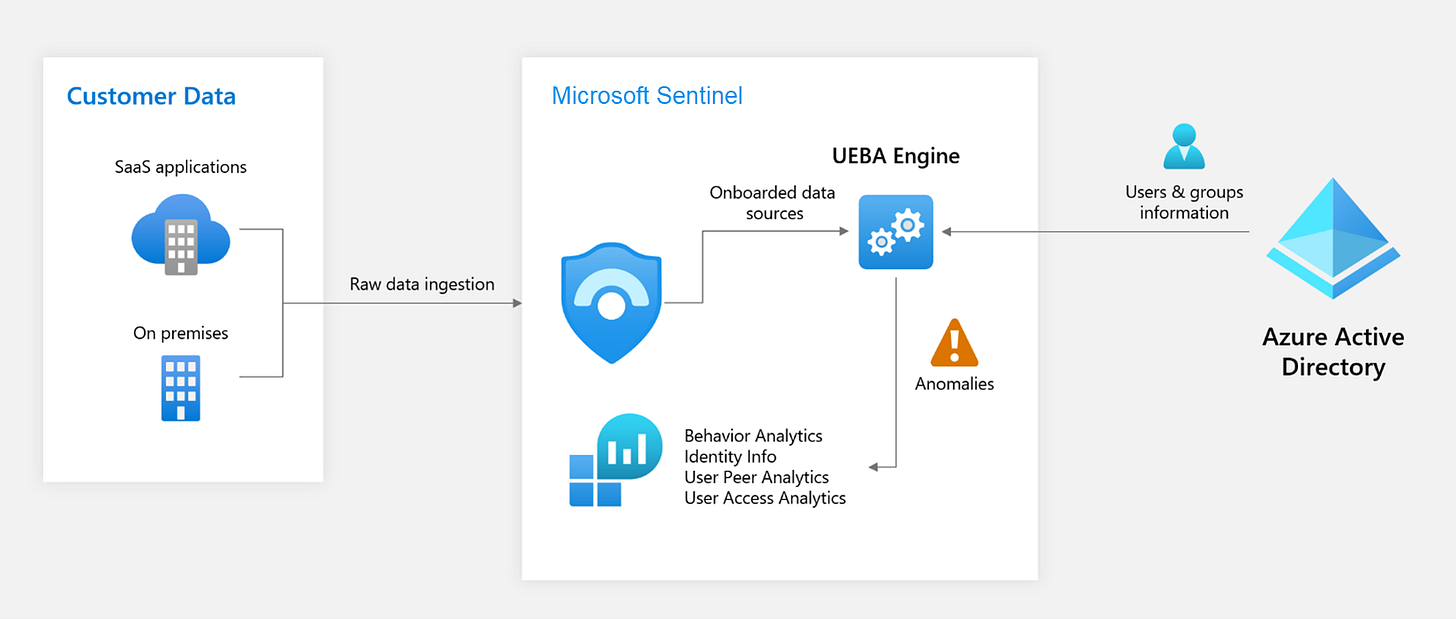
Let’s break down how the UEBA works from front to back.
Data Collection: Microsoft Sentinel collects data from various sources, including logs, events, and threat intelligence feeds. UEBA can also collect from Third-party systems and clouds such as on-premises firewalls, AWS, GCP, or Intrusion Detection Systems.
Data Processing: The collected data is processed and normalized to extract relevant entities (e.g., users, devices) and events (e.g., logins, file access). Event correlation and aggregation starts happening at this stage.
Behavioral Profiling and Anomaly Detection: The UEBA engine creates behavioral profiles for each user and entity, capturing their normal behavior patterns. Sentinel leverages machine learning algorithms help identify these patterns against threat intelligence sources and the entity profile, looking for anomalies amongst entity-related data such as location and time period.
Risk Scoring: The UEBA engine assigns a risk score to each user and entity based on their behavior, taking into account factors like anomaly detection, threat intelligence, and user attributes. Risk scoring is continuously updated as new data is ingested and processed.
Alerting and Investigation: When a user or entity exceeds a predefined risk threshold, Microsoft Sentinel generates an alert, allowing security analysts to investigate and respond to potential security threats.
How do I turn it on and use it?
Activating the UEBA features is really straight forward.
First, some prerequisites:
A Sentinel Workspace 😎
Global Admin or Security Admin Entra ID Roles
Microsoft Sentinel Contributor or Log Analytics Contributor Azure roles
Second, how to turn it on:
Login to the Azure Portal
In the search bar at the top, Search for and click on Sentinel, then select your workspace.
From the Sentinel main page, select “Settings” in the Configuration section on the left-hand flyout.
Inside the “Settings” window, select the “Settings” tab and click “Set UEBA” under “Entity Behavior Analytics”
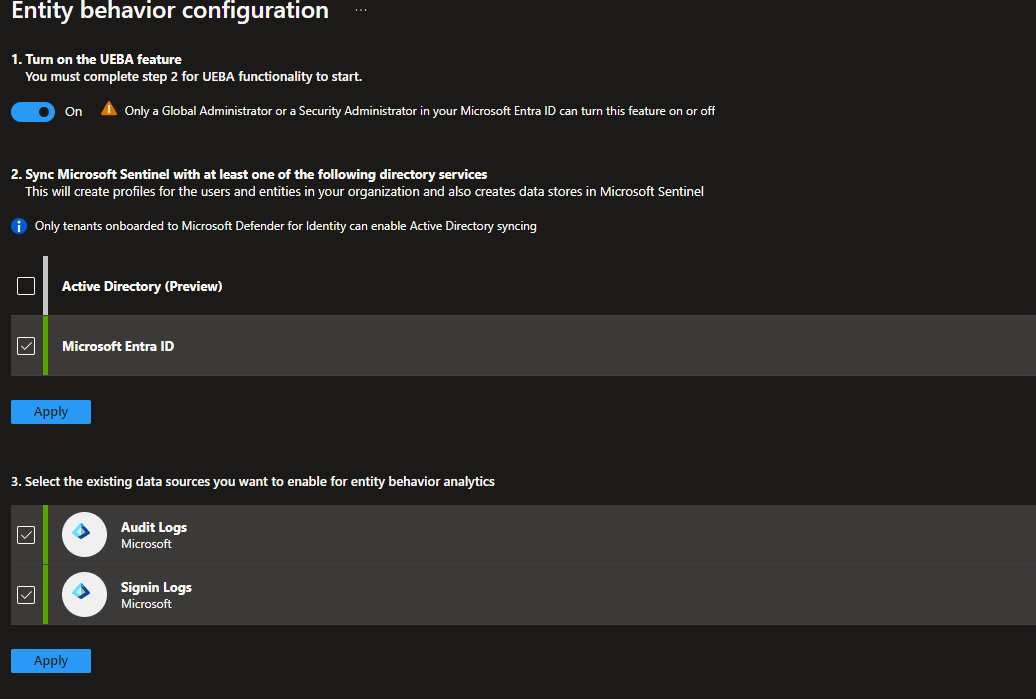
In the “Entity behavior configuration” menu, flip the “Turn on UEBA feature” to “On”
Make sure you select the directory service you want to sync entities from. I use Microsoft Entra ID for my tenant.
Next, select the data sources you want to enable behavior analytics with. Right now, I just have Audit and Sign-in logs while I continue to configure other features in this Tenant.
Done! UEBA is active and ready to start building those entity profiles!
Checking out your UEBA Data
Once UEBA is active, you might want to visualize your data and alerts. Right now, there are two main ways that I do that.
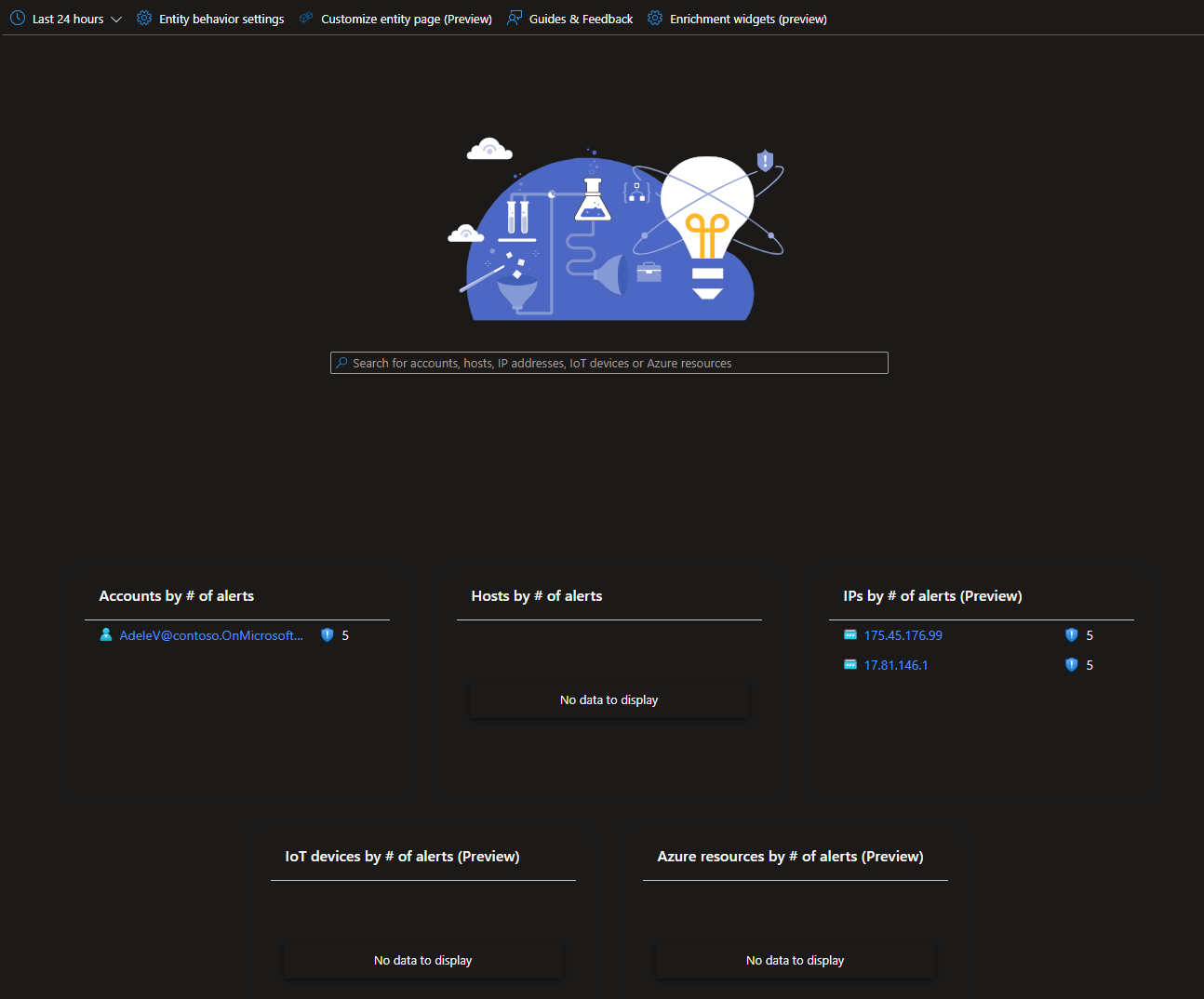
Entity Behavior Dashboard: The “Entity Behavior” menu in the Threat Management section of Sentinel is a built-in dashboard that will give you a way to search for entities and provides a breakdown of alerts by entity type. The best part of the is dashboard is that it can be extended with “Enrichment Widgets”, which provides access to supported third-party APIs that can enrich entity data in your environment. Currently available out of the box is VirusTotal, Recorded Future, Anomali, and AbuseIPDB.
UEBA Workbook from the Content Hub: Within the content hub inside Sentinel, you can install the “User and Entity Behavior Analytics” workbook. This provides a template Workbook that can help you visualize your UEBA data using KQL queries in a single page. The benefit with the workbook is that, because each section is backed by code, you can modify the Workbook to better display the data that is important to you!
Summary
In short, User and Entity Behavior Analytics (UEBA) compiles data from multiple sources to create baseline profiles for entities in your organization. Entities can include IP address, host devices, users, and applications. These profiles are created by combining entity related behavior with machine learning models to create a baseline, allow sentinel to allocate a risk score to behaviors that don’t meet the baseline. This provides SOC Analysts and Threat Hunters with an advanced toolset to monitor entities against their baselines and catch potentially malicious activity before an incident takes place!
Resources
Enable entity behavior analytics to detect advanced threats | Microsoft Learn
New updated version of the User and Entitity Behavior Analytics workbook (microsoft.com)